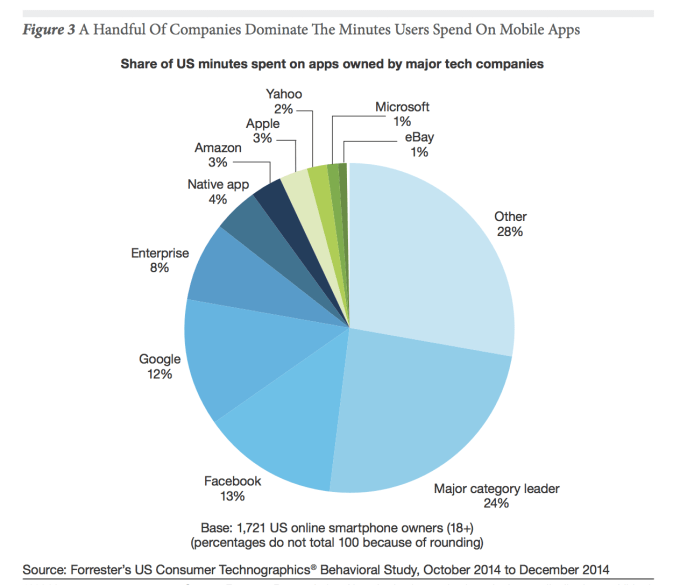
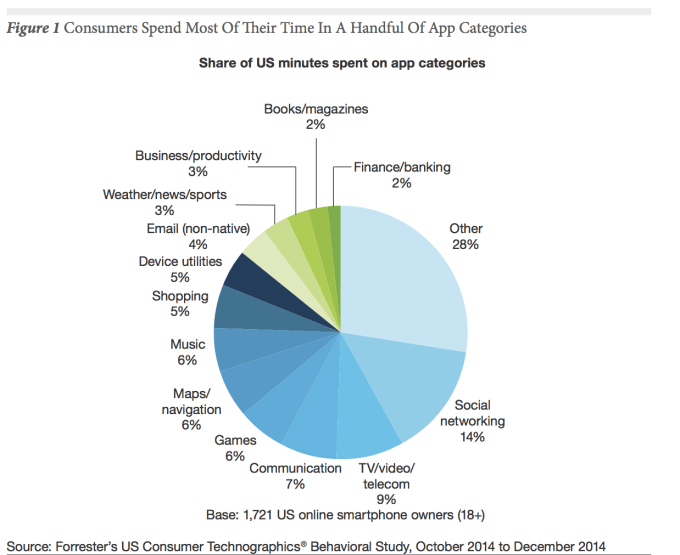
As reported by Robotic Trends: Listen, I’m all for personal freedom and less government infringement on our everyday lives. But the current wildfires sweeping across California are a perfect example, unfortunately, as to why stricter consumer drone regulation might be needed.
In the last week, state and federal firefighters have fought more than 270 wildfires in California alone. One fire burned nearly 18,000 acres of land and cost more than $7 million to contain.
Here’s the problem: firefighters are seeing more unauthorized consumer drones flying over active wildfires. Maybe the drone owners don’t know or maybe they don’t care, but temporary flight restrictions are placed over wildfire areas due to the aircraft used to help contain the fires.
Aircraft is used during wildfires to knock down flames and survey the burn area. When drones are in that restricted airspace, they’re in the path of aircraft.
In the last week, state and federal firefighters have fought more than 270 wildfires in California alone. One fire burned nearly 18,000 acres of land and cost more than $7 million to contain.
Here’s the problem: firefighters are seeing more unauthorized consumer drones flying over active wildfires. Maybe the drone owners don’t know or maybe they don’t care, but temporary flight restrictions are placed over wildfire areas due to the aircraft used to help contain the fires.
Aircraft is used during wildfires to knock down flames and survey the burn area. When drones are in that restricted airspace, they’re in the path of aircraft.
“A couple times yesterday we noticed some drones in our airspace,” said Cal Fire’s Steve Kaufmann (watch the KSEE video below).“I can’t encourage the public enough that when we have a fire in the area, they really need to try to have restraint.”
“Some of the hobbyist drones will get up in the air, and if their drone is in the air, we actually have to cease our air operations until we can get our arms around that,” he added.
The near-collisions between drones and commercial airplanes was enough to get the Consumer Drone Safety Act introduced, can you imagine the negative effects one crash, or one wildfire spiraling even further out of control, could have on hobbyist drones?
If you need more evidence of how some drone hobbyists are crossing the line, check out the video below, which you might have already seen, of John Thompson flying his drone over an active house fire. Eventually a firefighter sprays the drone (12 minutes into the video) and forces Thompson to fly away. Thompson took to Facebook and accused the firefighters of misconduct and said he would bill them to replace the $2,200 drone.
Thankfully, many commenters said Thompson was in the wrong. Again, I’m all for a laissez-faire system when it comes to flying consumer drones, but if we can’t police ourselves, we’re only asking for stricter regulation.
“Some of the hobbyist drones will get up in the air, and if their drone is in the air, we actually have to cease our air operations until we can get our arms around that,” he added.
The near-collisions between drones and commercial airplanes was enough to get the Consumer Drone Safety Act introduced, can you imagine the negative effects one crash, or one wildfire spiraling even further out of control, could have on hobbyist drones?
If you need more evidence of how some drone hobbyists are crossing the line, check out the video below, which you might have already seen, of John Thompson flying his drone over an active house fire. Eventually a firefighter sprays the drone (12 minutes into the video) and forces Thompson to fly away. Thompson took to Facebook and accused the firefighters of misconduct and said he would bill them to replace the $2,200 drone.
Thankfully, many commenters said Thompson was in the wrong. Again, I’m all for a laissez-faire system when it comes to flying consumer drones, but if we can’t police ourselves, we’re only asking for stricter regulation.